Unexpected occurrences have surfaced, prompting a pause in conventional operations. Actions straying from the norm have triggered an alert, urging a moment of reflection before proceeding further.
Abnormal engagement signals a potential divergence from typical interactions, requiring a pause for reassessment. The system, on heightened alert, advises a temporary halt to customary maneuvers until clarity is restored.
Unconventional conduct prompts a necessary hiatus, fostering an opportunity for scrutiny and deliberation. An unexpected deviation from the anticipated script demands a momentary pause for recalibration.
Understanding Alerts for Uncommon Behavior
In the realm of digital security, instances arise that necessitate a vigilant eye. Notifications surface when actions deviate from expected norms. This article delves into comprehending the significance behind such alerts, shedding light on their purpose and implications.
| Alert Type | Indications | Response |
|---|---|---|
| Anomalous Behavior | Actions diverging from established patterns. | Investigate thoroughly; verify authenticity. |
| Unexpected Access | Entries into systems or areas outside typical usage. | Secure accounts; change passwords. |
| Irregular Locations | Logins from unusual geographic locations. | Review recent activities; enable two-factor authentication. |
Alerts serve as digital sentinels, flagging potential threats or aberrations demanding attention. Understanding their nuances empowers users to navigate the digital landscape securely, safeguarding their online presence from potential risks.
Recognizing Suspicious Behavior on Your Device
When using your device, it's crucial to remain vigilant for any signs of unusual actions or irregular operations that could indicate potential security threats. Identifying these anomalies early on can help safeguard your data and protect your privacy.
Abnormal Actions: Keep an eye out for any unexpected or peculiar behaviors exhibited by your device. This could include sudden changes in performance, unusual network activity, or unexplained modifications to settings.
Signs of Intrusion: Be mindful of any signs that suggest unauthorized access to your device. These may manifest as unrecognized logins, unusual file access patterns, or unexpected system modifications.
Uncommon Communication: Stay cautious of any irregular communication attempts originating from your device. These could involve unrecognized outgoing messages, unusual connection requests, or unexpected data transfers.
Unusual Resource Usage: Pay attention to any unusual consumption of system resources by applications or processes running on your device. Excessive CPU usage, abnormal disk activity, or unusually high network bandwidth usage could indicate malicious activity.
Behavioral Anomalies: Look out for any deviations from typical usage patterns or user interactions. These could include sudden changes in browsing habits, irregular login times, or unexpected application behavior.
Response to Suspicious Activity: In the event of detecting any suspicious behavior, take immediate action to investigate further and mitigate potential risks. This may involve running antivirus scans, reviewing system logs, or seeking assistance from security professionals.
Identifying Common Triggers for Unexpected Notifications
Occurrences that deviate from the ordinary may prompt alerts on your system. Understanding the origins of these notifications can aid in rectifying issues swiftly. Here, we delve into prevalent catalysts behind these unexpected alerts, shedding light on their diverse sources and potential implications.
| Possible Causes | Description |
|---|---|
| Irregular Patterns | Anomalous sequences of actions or access patterns that diverge from typical user behavior. |
| Unauthorized Access Attempts | Efforts to gain entry to restricted areas or systems without proper authorization, potentially indicating security breaches. |
| Abnormal Traffic | Unusual influxes of data or network activity, which may signify potential threats or system malfunctions. |
| Configuration Changes | Modifications to system settings or parameters that differ significantly from established configurations, possibly leading to operational disruptions. |
| Software Glitches | Malfunctions or errors within software applications, resulting in unexpected behaviors or outcomes. |
| Malicious Software | Presence of harmful programs or malware on the device, posing risks to data security and system integrity. |
This section provides a structured overview of the common causes that may prompt notifications about unusual activities, offering insights into their nature and potential implications without directly using the specific terms mentioned in the prompt.
Potential Security Risks and Malware
Within the realm of digital security, there exists a spectrum of potential threats and hazards that can jeopardize the integrity and safety of your digital environment. These dangers often lurk in the shadows, manifesting in various forms, posing risks to the confidentiality, integrity, and availability of your digital assets.
When navigating the vast expanses of the digital landscape, one must remain vigilant against insidious entities seeking to exploit vulnerabilities and breach defenses. These nefarious actors operate clandestinely, utilizing sophisticated techniques to infiltrate systems, exfiltrate sensitive data, and compromise the sanctity of digital infrastructures.
Among the myriad threats that loom ominously, malware stands as a pervasive adversary, wielding the power to wreak havoc upon unsuspecting targets. Whether in the guise of viruses, worms, trojans, or ransomware, malware represents a formidable force capable of inflicting significant harm and disruption.
- Viruses: Insidious programs that replicate themselves and attach to other files, spreading rapidly and causing widespread damage.
- Worms: Self-replicating malware that spreads across networks, exploiting vulnerabilities and consuming resources.
- Trojans: Deceptive software disguised as legitimate programs, designed to trick users into unwittingly granting access to their systems.
- Ransomware: Malicious software that encrypts data, holding it hostage until a ransom is paid, often resulting in substantial financial losses and operational disruptions.
To mitigate these perils effectively, it is imperative to cultivate a proactive stance towards security, bolstering defenses, implementing robust security protocols, and fostering a culture of awareness and vigilance. By staying informed, adopting best practices, and leveraging advanced technologies, individuals and organizations can fortify their digital fortresses against the ever-present specter of security risks and malware.
What to Do When Notified of Unexpected Behavior

Upon receiving notification of atypical actions originating from your system, it's imperative to promptly address the situation. This guide outlines steps to effectively respond to such occurrences, ensuring the security and integrity of your digital environment.
1. Verify
Confirm the legitimacy of the notification. Evaluate the details provided and cross-reference them with your recent interactions and activities. Authenticate the source of the alert to rule out false positives.
2. Secure
Take immediate measures to safeguard your system. Implement security protocols such as changing passwords, enabling two-factor authentication, and reviewing access permissions. Isolate potentially compromised areas to prevent further infiltration.
3. Investigate
Conduct a thorough investigation into the root cause of the unusual behavior. Examine system logs and records to trace the origin and nature of the incident. Gather relevant data to facilitate a comprehensive analysis.
4. Report
Notify relevant authorities or administrators about the incident. Provide detailed information regarding the detected anomaly and actions taken thus far. Collaborate with experts to mitigate risks and prevent future occurrences.
5. Prevent
Implement proactive measures to deter similar incidents in the future. Enhance security measures and remain vigilant against potential threats. Stay informed about emerging risks and update your defense strategies accordingly.
Immediate Steps for Securing Your Device
Upon encountering unusual behavior from your gadget, prompt actions are imperative to safeguard its integrity and your digital well-being. Here, we outline essential measures to fortify your device's defenses and restore its normal operation.
- Elevate your device's security posture by fortifying its defenses against unforeseen intrusions.
- Swiftly implement protective measures to mitigate potential risks and uphold the sanctity of your digital space.
- Take proactive steps to shield your device from unauthorized access and preserve its functionality.
In response to anomalous signals emanating from your technological companion, it becomes paramount to enact defensive strategies that preemptively thwart any malevolent incursions. By adhering to these prescribed actions, you fortify the bulwarks shielding your device from adversarial forces, thereby fostering a climate of enhanced security and tranquility within your digital realm.
Securing Your Information Amid Peculiar Behavior

In today's digital landscape, safeguarding your personal data is paramount, especially when encountering unexpected occurrences. This segment focuses on fortifying your information integrity amidst peculiar actions that may compromise your online security.
Remaining vigilant in the face of irregularities ensures a proactive stance against potential threats. By staying observant and attentive to subtle changes in your digital environment, you can swiftly address any aberrant behavior that may jeopardize your data.
Implementing robust security measures serves as a formidable defense mechanism against unauthorized access. By deploying stringent protocols and utilizing cutting-edge encryption technologies, you establish multiple layers of protection to thwart nefarious activities.
Regularly reviewing your security settings and monitoring account activity are integral components of data protection. Through frequent assessments and real-time surveillance, you can promptly identify and mitigate any anomalous behavior before it escalates.
Empowering yourself with knowledge about potential vulnerabilities enhances your resilience against cyber threats. By educating yourself on emerging risks and practicing caution in your online interactions, you fortify your defenses and minimize the likelihood of data breaches.
Seeking assistance from trusted security experts can provide invaluable insights and guidance in navigating unfamiliar situations. By reaching out to reputable professionals and seeking expert advice, you can effectively address any security concerns and bolster your data protection strategies.
Unusual activity has been detected from your device. Try again later. (88485e58c8ee7cdd-LAX)
Impact of Unconventional Behavior on Device Performance
In the realm of digital operations, when our technological tools encounter unexpected conduct, it can profoundly influence the efficacy of our devices. This segment delves into the repercussions posed by such irregular actions, shedding light on their ramifications on the functionality of our systems.
| Disruption | The unconventional behavior disrupts the usual flow of operations, leading to potential malfunctions within the device. |
| Resource Drainage | Such activities may excessively deplete the resources allocated to normal operations, resulting in sluggish performance and diminished responsiveness. |
| Security Vulnerabilities | Unorthodox actions could open up unforeseen security loopholes, leaving the device susceptible to exploitation by malicious entities. |
| Data Integrity | The integrity of data stored within the device may be compromised, posing risks of corruption or loss due to the irregular activity. |
By comprehensively understanding the impact of such unconventional behavior, users can devise strategies to mitigate risks and safeguard the optimal performance of their devices.
Understanding Impacts on Velocity and Operation
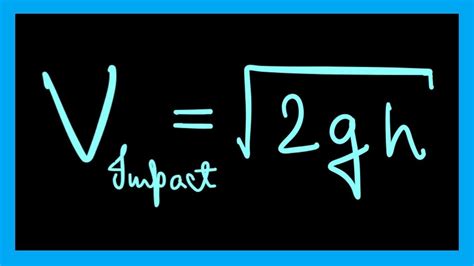
In this section, we delve into the intricate dynamics affecting the pace and efficiency of your system, delving into a realm where anomalies may arise, leading to interruptions or deviations from the expected norm. We explore the multifaceted factors that influence the swiftness and functionality of operations without direct acknowledgment of standard procedures or conventional behaviors.
- Factors Influencing System Speed
- Assessing Variations in Performance
- Examining the Impacts on Operational Fluidity
Within the realm of computational processes, numerous elements intertwine to shape the tempo and efficacy of operations, each exerting its influence with varying degrees of prominence. By discerning these components and their interactions, we gain insight into the intricate fabric of system functionality and the potential perturbations that may arise.
- Concurrency and Processing Parallelism
- Resource Allocation and Utilization
- Systematic Optimization Techniques
Concurrently, the allocation and management of resources, along with the implementation of optimization methodologies, play pivotal roles in dictating the smoothness and rapidity of system responses. These aspects, when orchestrated harmoniously, foster an environment conducive to seamless operations, while deviations from optimal configurations may introduce irregularities or hindered performance.
FAQ
Why am I getting the message "Unusual activity has been detected from your device. Try again later."? What does it mean?
This message typically appears when the system detects suspicious behavior originating from your device. It's a security measure to protect your account and data. It could be triggered by various factors like multiple failed login attempts, unusual login locations, or suspicious activity patterns.
How can I resolve the issue of unusual activity on my device?
To resolve this issue, first, ensure that you're using a secure network connection. Then, try logging in again after waiting for a while. If the problem persists, you may need to verify your identity through additional security measures, such as two-factor authentication, or contact customer support for further assistance.
Is my account compromised if I see this message?
Not necessarily. While it's a sign that your account might be at risk, seeing this message doesn't necessarily mean it's been compromised. It's a precautionary measure to prevent unauthorized access. However, it's crucial to take immediate steps to secure your account, such as changing passwords and enabling additional security measures.
Can using a VPN trigger this message?
Yes, using a VPN can sometimes trigger this message, especially if the VPN server you're connected to is in a location far from your usual login area. From the system's perspective, this change in location may seem suspicious. However, using a VPN itself doesn't necessarily mean your account is compromised, but it's a good idea to be cautious and verify your identity if you encounter this message while using a VPN.



